VSS Integration: Strengthening OCI (Oracle Cloud Infrastructure) Security with VSS (Vulnerability Scanning Service.
Introduction
In today’s digital world, security is a top concern due to the increasing risk of cyber-attacks and malware. To tackle these threats, OCI offers a helpful tool called VSS.
VSS does not cost you extra, it is a free addition to OCI. This positions it as a wise selection for reinforcing security in OCI instances and storage tiers. So, integrating VSS into OCI is essential to keep your digital assets safe from the ever-changing landscape of cyber threats.
OCI’s free Vulnerability Scanning Service automates quick host/port scanning for rapid identification and remediation of vulnerabilities, using recipes to define scanning parameters and targets to specify resources to be scanned.
Why Use VSS in OCI
- Proactive vulnerability detection: VSS scans your compute instances, container images, and DevOps Java builds for known vulnerabilities, identifying potential security weaknesses before attackers exploit them.
- Cost-effective: VSS is a free service within OCI, providing a valuable security tool without additional financial burden.
- Reduced manual effort: Eliminate tedious manual vulnerability assessments and patch management, freeing up valuable resources for other tasks.
Pre-requisite for VSS In OCI
- OCI Identity and Access Management (IAM) Policies
- OCI Compartment: VSS operates at the compartment level, so ensure that your target resources and VSS configuration are within the same compartment.
- Understanding Scan Scope and Requirements
- Vulnerability Scanning Recipes:
- Target Resources
- Supported OCI Regions: OCI region you are working in supports the Vulnerability Scanning Service.
Configuring Vulnerability Scanning Service in OCI
Accessing the Scanning in OCI Console
Log in to the OCI Console–> Navigate Identity & Security –>Scanning.
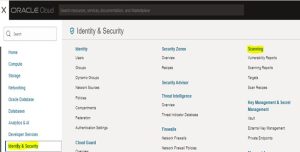
Under scanning –>Click Scan Recipes
Create scan recipe panel in one of the following ways.
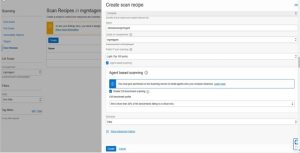
- Verify that the recipe type is Compute.
- Enter a name for the recipe.
Select the level of public IP port scanning for this recipe.
- Standard: Check the 1,000 most common port numbers.
- Light (default): Check the 100 most common port numbers.
- None: Don’t check for open ports.
Agent based scanning check box–> Disabling agent-based scanning means that you don’t want to activate the Vulnerability Scanning service against any targets assigned to this recipe.
Compute Scan Recipe with an OCI Agent
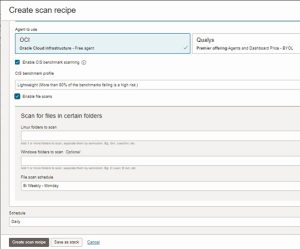
- Select Enable file scans to scan specific folders for vulnerabilities in third-party applications (Optional).
- For Linux folders to scan, specify at least one folder to scan on target Linux hosts.
Separate multiple folders using semicolons.
- Configure a File scan schedule. Choose from Bi-weekly or Monthly.
- The schedule controls how often the targets assigned to this recipe are scanned. Choose Daily or one of the Weekly values.
After creating a recipe, you can create scan targets and associate them with the recipe.
At least one Compute scan recipe must be in the tenancy before creating a target.
Navigate Identity & Security–>Scanning–>Targets–>click Create Target
Verify that the recipe type is Compute.
Enter a name->Create in which compartment->select required scan recipe for the Target
- Choose the instance for this target.
Can select all instances or single instance based on the requirement.
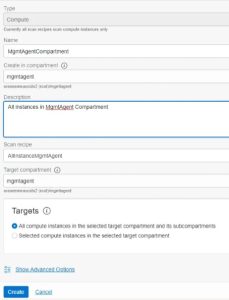
- Click Create target to create the recipe in Vulnerability Scanning.
After creating a target, Vulnerability Scanning checks the instances for security vulnerabilities and open ports based on the parameters and schedule that’s configured in the recipe. We can view the results of these scans in the Vulnerability and Scanning Reports
Conclusion
By implementing VSS in OCI we not only identify and address potential security threats proactively but also establish a resilient foundation for safeguarding sensitive data and critical infrastructure. This strategic integration reinforces a comprehensive security framework, aligning with industry best practices and ensuring a robust defense against evolving cyber threats.
