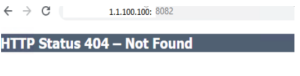
Configure tomcat web server to prevent information leakage:
Problem Description:
This information can help an attacker gain a greater understanding of the systems in use and potentially develop further attacks targeted at the specific version of IIS. An attacker might use the disclosed information to harvest specific security vulnerabilities for the version identified.
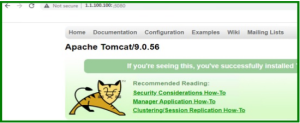
Solution:
Configure our tomcat web server to prevent information leakage from the SERVER header of its HTTP response.
Steps:
- Go to the tomcat install directory:
<install-directory>/conf/web.xml
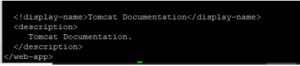
- Comment the welcome pages index file in web.xml file:
<!–
<welcome-file-list>
<welcome-file>index.html</welcome-file>
<welcome-file>index.htm</welcome-file>
<welcome-file>index.jsp</welcome-file>
</welcome-file-list>
–>
- Edit the file <install-directory>/conf/server.xml
- Search for the parameters <Host name=
Just below that line, insert the following parameters
<Valve className=”org.apache.catalina.valves.ErrorReportValve” showReport=”false” showServerInfo=”false” />
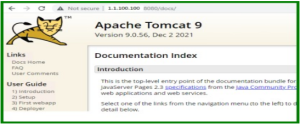
- Go to docs directiory <install-directory>/webapps/docs/WEB-INF/web.xml
Comment that tomcat documentation files.
- Bounce the tomcat servers.
- After all changes done the we have hide the tomcat server information leakage.