In today’s fast-paced digital landscape, the importance of database security cannot be overstated. For leaders across your organization—be it a CEO guiding overall strategy, a CTO focused on technology innovation, or a DBA dedicated to maintaining data integrity—ensuring the security of your databases is critical. A single breach has the potential to not only disrupt operations but also cause significant harm to company reputation.
Introduction to Oracle’s Database Security Assessment Tool (DBSAT):
Oracle’s Database Security Assessment Tool (DBSAT) Offered at no cost, empowers organizations to assess their database security comprehensively, identify vulnerabilities, and measure their compliance against various security standards and enhance your database security posture. Whether you’re aiming to mitigate common security risks or identify sensitive data within your databases, DBSAT is a valuable tool that makes it easier to uncover potential vulnerabilities and enhance your security framework.
Why Should You Consider DBSAT?
Implementing DBSAT within your security protocols offers a multitude of benefits for your database environment:
- Comprehensive Security Assessment: DBSAT enables you to quickly evaluate your current security status, ensuring that all sensitive data within your Oracle databases is identified and protected.
- Risk Mitigation: By adhering to Oracle’s proven security best practices, CIS Benchmark recommendations, and Security Technical Implementation Guides (STIG) rules, you can significantly reduce your organization’s risk exposure.
- Regulatory Compliance: DBSAT’s detailed security findings facilitate compliance with stringent regulations, such as the EU GDPR, by highlighting areas that need attention.
- Enhanced Security Posture: Regular use of DBSAT can greatly improve the overall security posture of your Oracle databases, fostering a culture of security best practices across your organization.
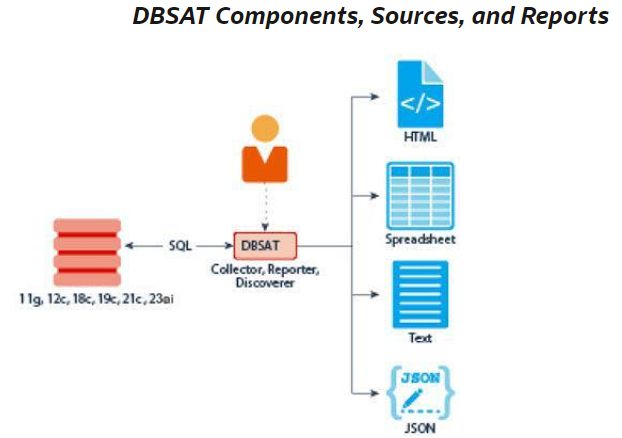
Understanding the Core Components of DBSAT

DBSAT is a simple tool composed of three main components:
- Collector: The Collector is the initial phase of DBSAT, responsible for gathering data. It executes SQL queries and runs operating system commands to collect information from the system under assessment. This data, primarily sourced from database dictionary views, is saved in a JSON file for further analysis. For the most comprehensive data collection, it is recommended that the Collector be run on the database server itself, as remote execution may omit certain operating system details.
- Reporter: Once data collection is complete, this component analyzes the collected data and generates a comprehensive Oracle Database Security Assessment Report. The report is available in multiple formats, including HTML, Excel, JSON, and Text, providing flexibility in how the findings are reviewed. The Reporter can be executed on any machine, whether it’s a PC, laptop, or server, offering convenience and accessibility.
- Discoverer: The final component, Discoverer, is tasked with identifying sensitive data within the database. It uses SQL queries to collect metadata, which is then compiled into the Oracle Database Sensitive Data Assessment Report. Like the Reporter, the Discoverer is versatile, able to run on any machine, making it a flexible tool.
Oracle Database Security Assessment Report
The DBSAT Reporter organizes its analysis into units called “Findings.” Each Finding includes several key elements that help you understand and prioritize security risks:
– Rule ID: Consisting of a prefix indicating the report section and a suffix identifying the specific rule.
– One-line Summary: A concise overview that highlights the purpose and context of each check.
– Status: The Status helps you gauge the severity of each finding, enabling you to prioritize actions accordingly:
– High Risk: Requires immediate attention.
– Medium Risk: Should be addressed in the short term.
– Low Risk: Can be managed during scheduled downtime or alongside other maintenance activities.
– Evaluate: Needs further manual analysis.
– Advisory: Suggests opportunities for improvement and alerts you to other available security controls within the Oracle Database.
– Pass: No risks were identified.
– Summary: Offers an overview of the Finding. For informational Findings, this section usually reports the number of data elements examined.
– Details: Provides in-depth information explaining the summary, often including results from the assessed database along with recommended changes.
– Remarks: Clarifies the rationale behind the rule and suggests actions for remediation.
– References: Lists relevant guidelines, such as Oracle Best Practices (OBP), Oracle Database 12c STIG V2R8, CIS Oracle Database Benchmark 12c v2.0.0 recommendations, or GDPR Articles/Recitals, if applicable.
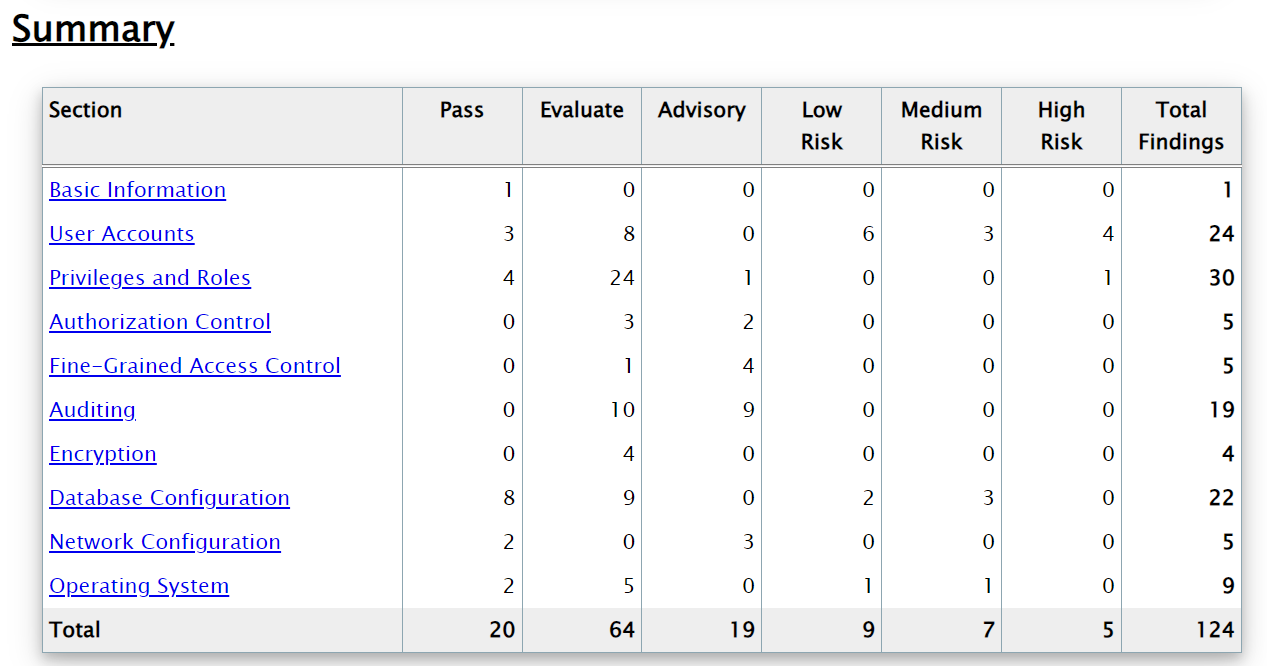
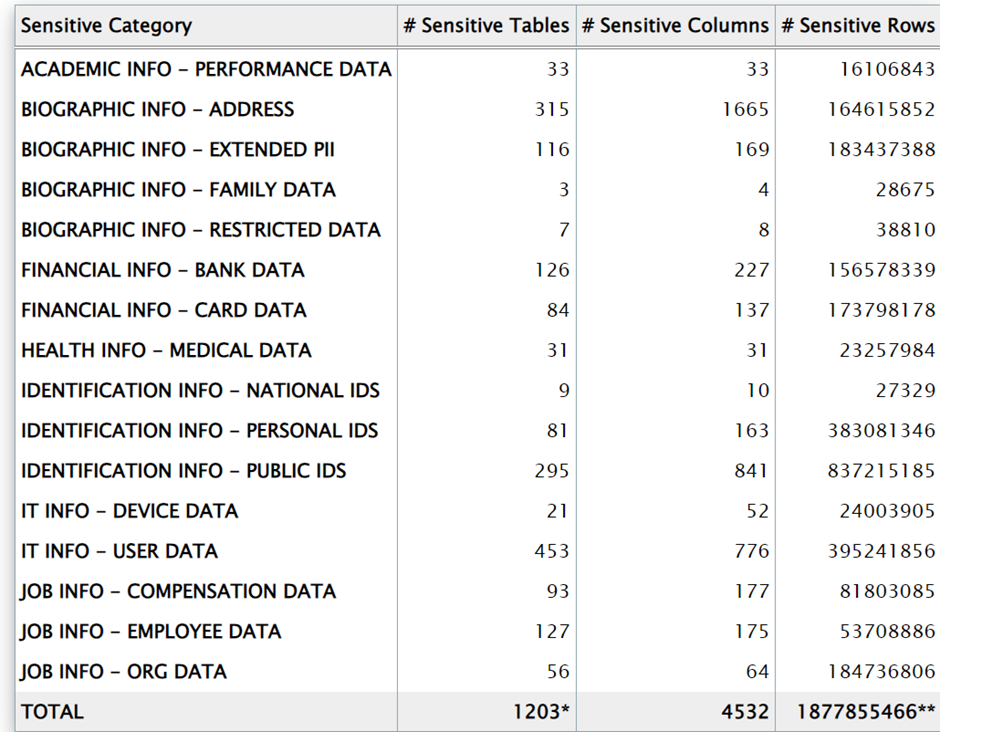
Here are the few outputs you can look at what you get from DBSAT:
Conclusion
In an era where data breaches are a constant threat, ensuring the security of your databases is not just a technical requirement but a strategic imperative. Oracle’s Database Security Assessment Tool provides a powerful, user-friendly solution to help you stay ahead of potential vulnerabilities. By leveraging DBSAT, you can protect your organization’s most critical asset—its data—while maintaining compliance with global security standards.
