Objective:
To renew and bind a new TLS certificate to SQL Server to ensure continued secure connections.
Frequency:
Annually or prior to certificate expiration
Prerequisites:
- Administrative access to the Windows Server hosting SQL Server
- Sysadmin privileges on SQL Server
- Access to the new TLS certificate (issued and installed)
- Certificate should have the Server AuthenticationEKU and the FQDN of the SQL Server in the subject or SAN
Steps:
1. Verify Current Certificate (Optional but recommended)
- Open SQL Server Configuration Manager
- Navigate to SQL Server Network Configuration→ Protocols for <InstanceName>
- Right-click Properties→ Certificate tab
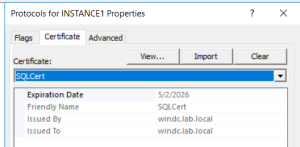
- Take backup of current certificate details
2. Install the New Certificate
- Open MMC(exe)
- Import the new certificate under: Personal→ Certificates
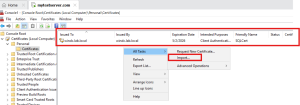
- Make sure the certificate has:
- Private key
- Server Authentication listed under Enhanced Key Usage
- The correct FQDN in the subject or SAN
- Assign Permissions to SQL Server Service Account on the Certificate
After importing the certificate, you must give the SQL Server service account permission to use the certificate’s private key, or SQL Server won’t be able to bind the certificate.
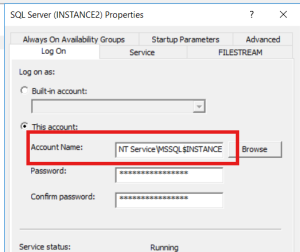
- Identify the SQL Server service account:
- Open SQL Server Configuration Manager
- Go to SQL Server Services
- Note the Log On As account for your SQL Server instance (e.g., NT Service\MSSQLSERVER or a domain account like DOMAIN\sqlsvcprod)
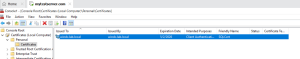
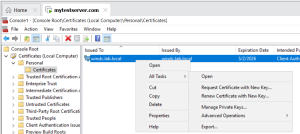
- Open Certificate Manager (MMC):
- Run msc to open the Local Machine certificate store.
- Navigate to: Personal → Certificates
- Locate the certificate you just installed.
- Open Certificate Permissions
- Right-click the certificate → All Tasks→ Manage Private Keys
- In the Permissions window: Click Add
- Enter the SQL Server service account name
- If it’s a built-in service account (e.g., NT Service\MSSQLSERVER), make sure to include the NT Service\
- Click Check Names to validate it.
- Once added, select the account and check Allow → Full Control
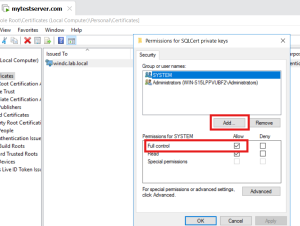
- Apply and Close:
- Click Apply and OK
- Close the MMC
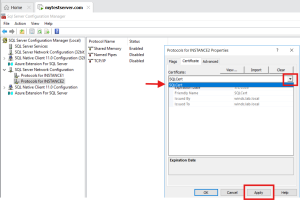
4. Assign Certificate in SQL Server Configuration Manager
Go to SQL Server Configuration Manager
Navigate to: SQL Server Network Configuration → Protocols for <InstanceName>
Right-click → Properties → Certificate tab
Choose the new certificate from the list
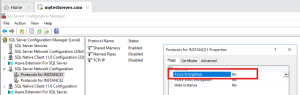
l Go to Flags tab and verify:
ü Force Encryption = Yes (if required by your security policy)
5. Restart SQL Server Service
- Go to SQL Server Services
- Right-click on SQL Server (<InstanceName>)→ Restart
- Optional: Restart SQL Server Agent if it’s in use
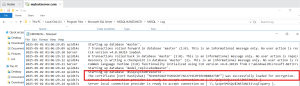
6. Verify the Certificate Binding
- Open SQL Server ERRORLOG
- Look for entries like:
- The certificate [Certificate Name] was successfully loaded for encryption
7. Cleanup
- Remove expired certificates from MMC to avoid confusion
Recent Posts
